Strategic Work Identification
Recently I’ve been thinking a lot about how to identify what work to spend time on.
All work can be evaluated across four main concepts: 1. Expertise: How good are you at the work? 2. Purposeful: How important is the work? 3. Fun: How much fun are you having doing it? 4. Difficult: How difficult is it for others to do this work?
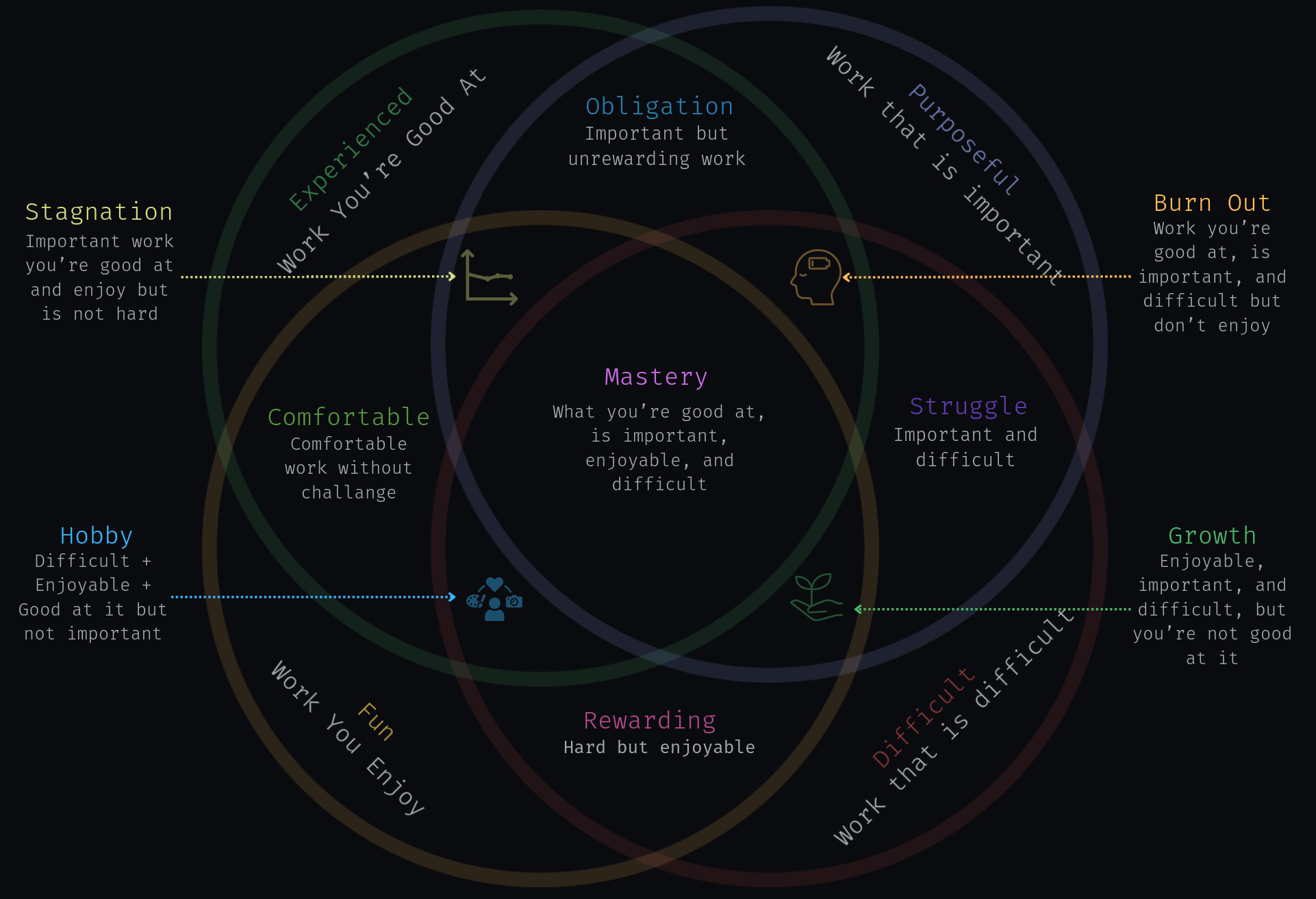
The first three are fairly standard and have been discussed before but through a non-security career related lens. - Ikigai: A concept that represents the intersection of what you love, what you’re good at, and what the world needs - Hedgehog concept: A concept that represents what you’re passionate about, what you can be the best in the world at, and what drives your economic engine (things you can make money from) - Flow theory: The idea that people do their best work when engaged in activities that balance skill and challenge
Why add difficulty to the mix? The idea is that if you can do something very difficult, you will have an advantage over everyone else. Being good at something that you find fun and fulling, and is exceptionally difficult is the best way to have have competitive advantage and guarantees job security.
How can this be used?
A thought exercise you can do is anytime you’re spending time on a task, identify where it falls in the venn diagram. How do you move the point it falls to be more towards the center?
Kubernetes Offensive Security Example
I’ve been spending a lot of time working in the realm of offensive Kubernetes security so here are some examples of work that would land in each zone.
Outer ring
- Experienced: Creating Kubernetes penetration testing environments - You’ve built hundreds of these, but they’re primarily for practice rather than production security.
- Purposeful: Implementing a vulnerability scanning program within a Kubernetes environment as someone who has never worked with Kubernetes.
- Fun: Experimenting with new Kubernetes attack chains in lab environments - Enjoyable exploratory work that might not have immediate business impact.
- Difficult: Digging through the Kubernetes source code - Challenging technical work that isn’t particularly enjoyable.
Single overlap
- Comfortable: Basic YAML configuration review of Kubernetes manifests - Routine work that provides some value but presents few new challenges.
- Obligation: Compliance documentation for Kubernetes security controls - Necessary for regulatory requirements but tedious and unrewarding.
- Struggle: Researching how to secure an outdated Kubernetes deployment that can’t be updated as someone who has never worked with Kubernetes - Critical and difficult work that requires skills you don’t have.
- Rewarding: Red team exercises against Kubernetes environments as someone that doesn’t know Kubernetes very well - Challenging and enjoyable to simulate attacks against production-like environments.
Double overlap
- Stagnation: Running automated Kubernetes vulnerability scanners - You’ve mastered these tools, scanning is essential, you enjoy finding issues, but it’s become routine and lacks challenge.
- Burn Out: Kubernetes incident response - You’re skilled at containing breaches in compromised clusters, it’s vital work with high technical complexity, but constant pressure and on-call rotations have made it draining.
- Hobby: Building Kubernetes CTF (Capture The Flag) challenges - Technically challenging, enjoyable, and you’re good at it, but not business-critical.
- Growth: Zero-day Kubernetes vulnerability research - Important, challenging, and exciting work where you’re still developing expertise.
Mastery
- Mastery: Building and leading an Kubernetes offensive security program that includes researching new attack paths - You’ve developed deep technical skills to identify vulnerabilities across the entire attack surface, your work directly protects critical infrastructure, you continuously face novel challenges as the ecosystem evolves, and you find genuine satisfaction in the creative problem-solving required to stay ahead of emerging threats.